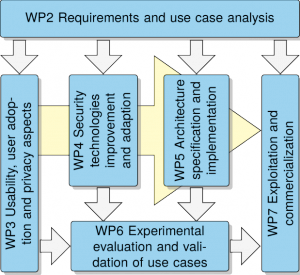
 The project CREDENTIAL is scheduled for 36 months and the work plan is defined in accordance with the objectives of the project, and organised according to the expertise of the partners. The work plan is organised in seven work packages and their relation and interdependencies is shown in the figure.
The project CREDENTIAL is scheduled for 36 months and the work plan is defined in accordance with the objectives of the project, and organised according to the expertise of the partners. The work plan is organised in seven work packages and their relation and interdependencies is shown in the figure.
WP1 is led by AIT, provides the coordination and project management to ensure proper achievement of project objectives, within the time scale and on budget.
WP2, led by FOKUS, aims at a comprehensive requirements elicitation and analysis of use cases to specify. Then the work package has to define business requirements as well as security and privacy requirements and conducts a risk and threat analysis. It also defines the scope of the wallet together with technical and functional requirements.
WP3, led by GUF, has the overall objective to promote the uptake of CREDENTIAL by end users and businesses. Therefore, it conducts research on usability and key factors for technology adoption. It guarantees for the usability of the developed cryptographic tools and systems, which is very important for the project impact. Moreover, this WP also covers in depth privacy analysis and holistic security-by-design guidance throughout the project to demonstrate and verify the increased security by the novel approach taken in CREDENTIAL.
WP4, led by TUG, covers the research aspects of CREDENTIAL as well as the specification of basic low level building block and tools used in subsequent developments. The work package is dedicated to the analysis and adaption of appropriate cryptographic methods for proxy encryption and data minimization as well as the review and selection of strong authentication means. These are the core technologies, which the novel privacy preserving features of the identity wallet are based on and they are combined in basic backend protocol specifications.
In WP5, which is led by ATOS, the architecture specification is done. All modules, important interfaces and protocols are defined and its integration/extension into existing IAM solutions is proposed. The general core modules are then implemented in high quality software modules and libraries which are then tested against a rough reference architecture implementation.
WP6 is led by OTE and aims at evaluation of CREDENTIAL results by experimental validation of the use cases specified in dedicated pilots. The results of WP6 will lead to recommendations for cryptographically sound secure identity service deployment based on CREDENTIAL tools and pave the way for exploitation after the project.
WP7 covers all dissemination, exploitation and commercialization activities and is led by KGH. To maximize the impact during project execution and after the project we have planned a substantial amount of resources for exploitation activities. We will develop a detailed business plan and an appropriate exploitation strategy together and make them available together with information and tools for software and protocol integration enablement. All task will be backed up by broad communication and dissemination activities of all partners. Moreover, partners affiliated with standardization bodies will push project results toward adoption in IAM standards used on the Internet.
Finally, WP8, led by AIT, is taking care of all ethical issues occurring during the project duration, in particular related to the possible collection of personal data during the piloting phase.
